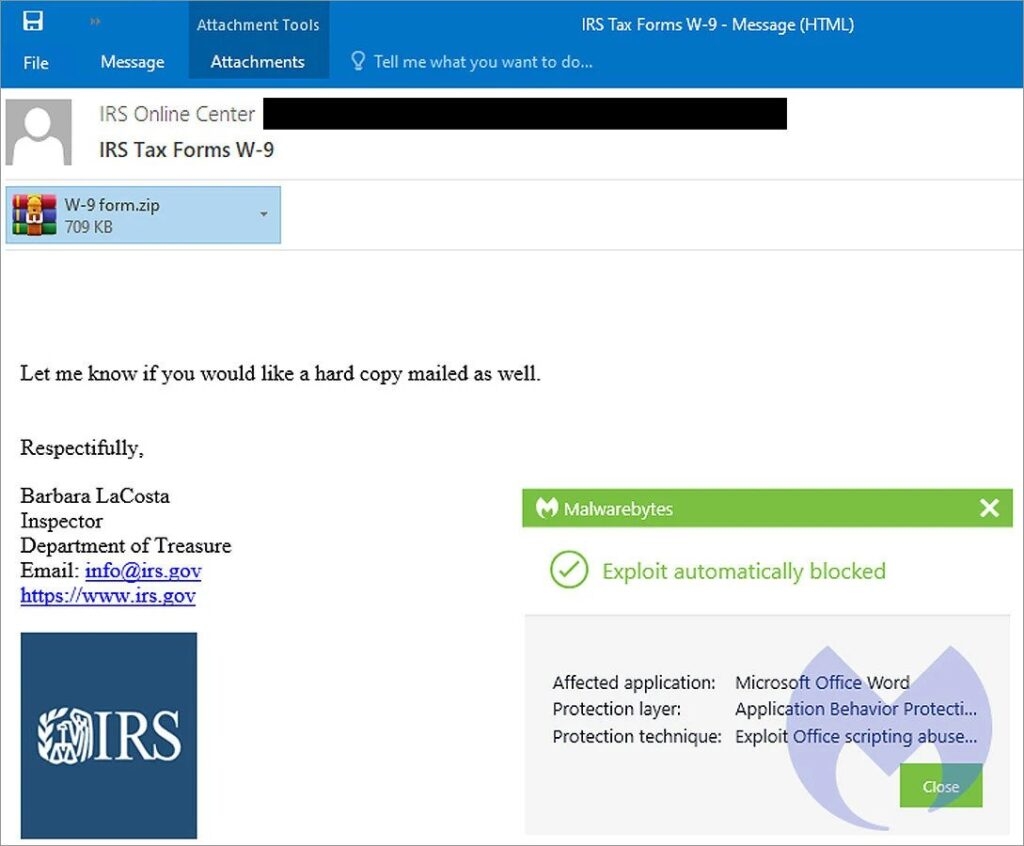
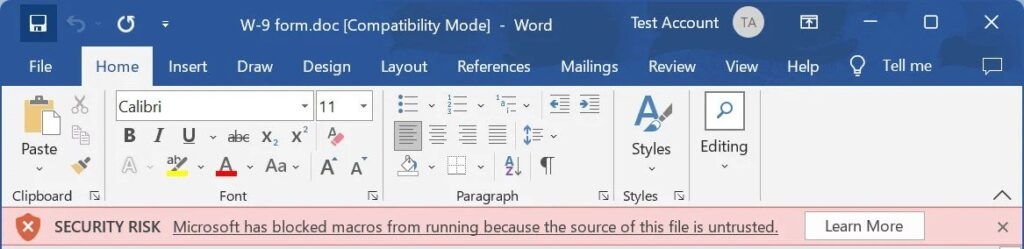
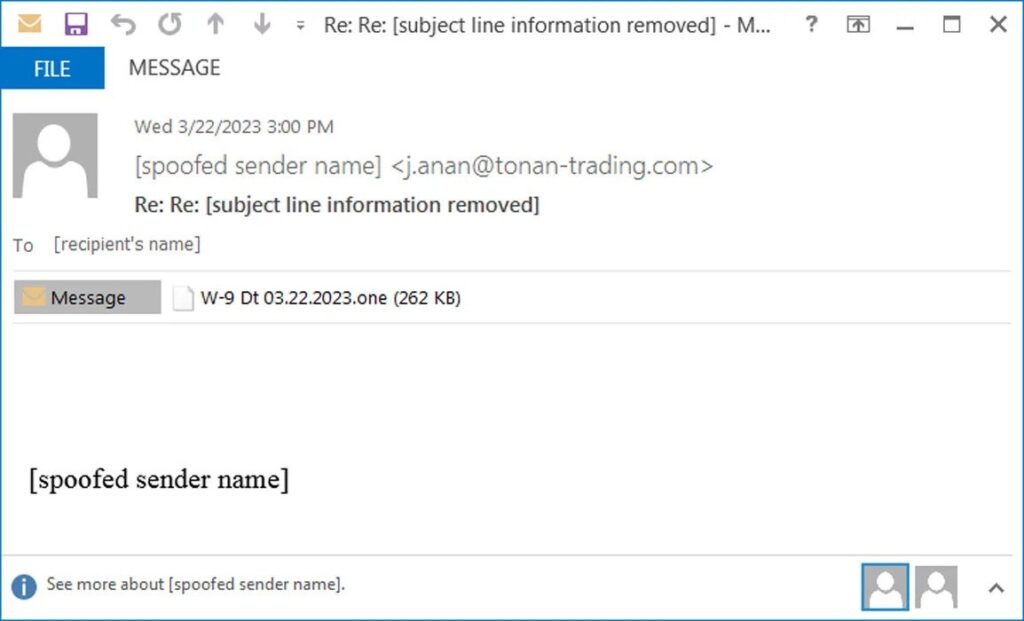
The Emotet is an infamous malware infection that is distributed through phishing emails that previously had Microsoft Word & Microsoft Excel documents with malicious macros that install the malware. However, as Microsoft now blocks the macros by default in downloaded Microsoft Word documents so the Emotet malware shifted to Microsoft OneNote with embedded scripts to install Emolett malware The attackers who operate Emotet generally use themed phishing campaigns to concur with the holidays and the yearly tax returns, i.e., The US tax season. As for the phishing campaign found by Malwarebytes, the attackers send emails with the subject “TRS Tax form W-9″ while impersonating an authority from Internal Renew Service. Read: Common Magic & Power Magic Malware Used in Advanced Surveillance Attacks These phishing emails have a ZIP archive named W-9 form.zip which contains a malicious word document. The document has been puffed up to 500MB to make it difficult for the security software to detect if it’s malicious. As the Emotet gets installed, the malware starts stealing the victim’s email for its future replay chain attacks and then spams emails & at the end, installs other malware that gives initial access to other threat actors as well. That said, since Microsoft now blocks macros by default, the users are less likely to go through the pain and enable macros and get infected by word documents. Now in the phishing activity found by the Palo Alto Unit 42, the attackers bypass these restrictions by using Microsoft OneNote Document with the enabled VBScript files that install the malware After that, the phishing activity utilizes the replay chain e-mail, which pretends to be the business partners sending victims the W-9 form. The attached OneNote Document will make it believe that it is protected and requests the user to double-click to view the document correctly, although what’s hidden inside is the View button which has VBScripts that will be launched instead.] When opening the embedded VBScript file, Microsoft OneNote warns the user that the file may be malicious, but unfortunately, as we know, many of the users simply ignore these warnings and allow the files to run. Once the files are executed, VBScript will download Emotet DLL and run it using the regsvr32.exe. After that, the malware runs quietly in the background, stealing e-mails and contacts and then waiting for a further payload to be installed onto the device. So if you get any email that claims to have the W-9 form or from any other tax forms, simply scan the document first with anti-virus software. Moreover, these forms are sent in as PDF attachments, not as Word attachments, so avoid opening them and enabling macros and rather delete the emails. Read: Fortinet Cyber Security Update Fails; Zero-Day Exploited by Threat Actors